What is with Unix and Users anyway?
What is with Unix and Users anyway?
A.K.A Unix User Control Process (UUCP :-)
"When a strong man armed keepeth his palace, his goods are in peace: But when a stronger than he shall come upon him, and overcome him, he taketh from him all his armour wherein he trusted, and divideth his spoils."
- Luke 1121-22 (The Living Bible)
We have all heard about hackers1 and hacking. Indeed the quotation above could have been made with respect to an hacker gaining access to a system illegally. But the true focus of this piece is not about hacking but a brief and simple explanation of the concept of computing systems, users and access control. We will be using a scenario from everyday life to make our explanation(s).
Let us proceed :-)
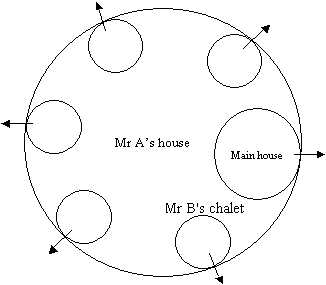
Mr. A's house
Mr A is a rich man who has a large house1 which is fenced around with many gates. In this compound of Mr A's, apart from the main house, there are five little chalets. Each Chalet is constructed such that it has an exit
gate2 (ports) out of the compound in the fence. Given a gate for the main house and one for each chalet, we can conclude that there are at least six gates built into the fence surrounding Mr A's house.
Mr A then leases out some of the chalets3 (services such as webserver). Also some of the rooms in the main house is occupied by a few of Mr A's closer
relatives4 (user accounts).
Since the chalets have many rooms each, we should assume that some of the more industrious tenants of Mr A's would lease out any rooms that they don't make use of - in short they obtain tenants of their own while they themselves are tenants of Mr A.
Mr A of course those not want to turn his own private quarters into a public place where all sorts of people may come and go as they please - including as always happens people with doubtable integrity and morals! So Mr A of course did the right thing by putting plenty of gates in his fence. He doesn't want a strange character coming to knock on the main house's door asking for one of his tenants. So Mr A is secure in the knowledge that unless you have business with someone in the main house, then you have no right to expect to be granted entrance to the main house. All well and good. But wait a minute! If Mr A's innocent cousin unsuspectingly brings home a rogue, it is highly undesirable to have them wandering around the main house! But Mr A is a smart fellow, so when building the house he made provisions for security and for restricting access to the more private areas of the house to only himself (root or superuser). He employed an incorruptible guard who watches over the whole house. The guard has a database (/etc/passwd file) of all the residents leaving in the house and specially chosen secrets (passwords) that they must give before he will allow them into any of the rooms - even their own rooms! Talk about security! Of course, it happens once in a while that one or the other of Mr A's live-in relations forgets his/her secret and would have to ask Mr A (system administrator) to persuade the guard to let him/her in (usually the systems admin changes the password to something new)
The Chalets
Mr B is one of Mr A's tenants and has a chalet all to himself5 (a webserver)- in which he runs a film centre where a lot of people come and go to buy and borrow cassettes (view webpages, submit/retrieve info via web applications - e.g., CGI scripts). Since Mr B has various types of films (some suitable for family viewing, others X-rated, some horror and so on) , he decided to borrow a leaf from the security facilities Mr A implemented in the main house. He decided to put various categories of films in different rooms (directories) and put in place a system of allowing access by a series of username and password combination. So that to gain access to any restricted film, Mr A must have deemed it right for you to do so and given you the right combination of username and password. Of course the unrestricted area is not passworded (e.g., informative websites and most companies websites)
Let us review what we have discussed:
1. Only people with valid username and passwords combination are allowed access to the main house.
= the superuser creates login accounts for users (useradd name-of-user) and assigns the user a password (passwd name-of-user) (these accounts are called system accounts)
This user can then login into the system (e.g. via TELNET or SSH) and be given access to his room (usually his home directory - a directory on the system where he can store his files)
And he is automatically given restricted access to the rest of the main house - he should be able to go to the loo at least! (/dev/null and /tmp for example)
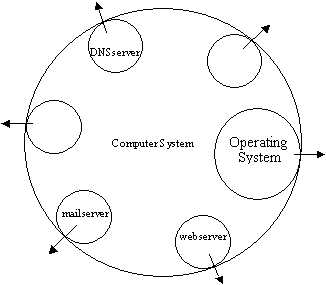
2. Mr A has tenants which run services
= a webserver, DNS server, mail server, database server etc running on the system. These services are allowed to institute a security system similar to the one used by the main system -i.e., they can in turn create user and passwords to control access to their own resources. Please note that these users and passwords cannot gain direct access to the system - only system accounts can do that (see 1 above)
3. Hacking revisited
Normally when there are security flaws in the services running on a system, hackers can exploit these flaws to gain access to the system itself and cause all sorts of damages.
Phew! That is all for now.
11:22PM 06/09/2003
Footnotes
A PORT is like a logical door. Actually it is a point of attachment to the network. Only
one service can listen on a particular port on a particular system on a
particular network (IP address). So when some data comes from the network, the
networking subsystem examines it and based on the port determines which service to hand the data to. Some
ports are 80 (web), 53 (DNS), 110 (POP3), 1521 (Oracle), 1645 and 1646 (RADIUS).
UUCP really means Unix to Unix Copy
1. Cracker is probably the better term for someone that gains access to a
computer system illegally for the purpose of doing damage to the system, or for
some other illegal use.
Description and use of Unix accounts management goes here (might never be
written :-)
useradd, userdel, passwd, gpasswd,
NOTE: This was never intended to be a technical piece. It was written in a couple
of hours as a means of introducing a colleague to the concept of Unix accounts.
All the errors and omissions are regrettably (not) mine. Gotcha!
12-Sept-2004
Back to main
page | Back to the top | Contact me | Favourite sites